ABOUT CONFERENCE

Cyber security 2020 uniquely addresses cyber security, cyber warfare and information warfare.For the past 15 years cyber security has developed into an important conference in the cyber-security field, attracting academics, military professionals and practitioners from around the world to present their research findings in the form of empirical studies, case histories and other theoretical and practical contributions. In addition doctoral degree candidates find this conference a valuable opportunity to network with others and have the opportunity to present papers and posters.
Over the years the Conference has been attended by a variety of security and military organisations including Cyber Security Policy Research Institute, more than 10 national defence colleges, NATO, SHAPE etc.
Information is power. And wherever there’s power, there are people looking to steal it. But that’s also where you’ll find us. We’re CYBER SECURITY 2020 Conference. And we’re here to stand against cyber threats around the world.
That means being here for you. Connecting you with the people and insights that will empower you to stay ahead of cyber threats. We do this through our online outreach and with our events around the globe.Some say it’s impossible to stay ahead of cyber security threats. We disagree. We’ll always be here as your go-to resource for exchanging ideas, learning the latest trends and finding the solutions for a more secure tomorrow.
career opportunity in cyber security
If you are planning to take some course on Cyber Security, make sure you look at the following points:
-
Industrial Association
-
Course Curriculum
-
Faculty
-
Live/capstone projects
-
Placements
Make sure you go for a course curriculum which gives the entire 360 degree view about Cyber Security.
Some famous colleges are:
-
Fanshawe college- St. Thomas/Elgin, Canada
-
Georgia Institute of Technology, USA
-
Aegis School of Cyber Security, India
-
Karlsruhe Institute of Technology, Germany
-
RMIT University, Australia
Target Audience
-
Scientists/Researchers
-
President/Vice president
-
Chairman’s/Directors
-
Professors, Data Analysts
-
Data Scientists
-
Experts and Delegates etc.
-
Heads, Deans, and Professors of Computer Science Departments
-
Research Scholar
-
Engineers
-
Consultants
-
Lab technicians
-
Founders and employees of the related companies
TRACK 1:Secure Passwords:
The keys to our digital kingdom, passwords should be closely protected. A lot of the times, that’s all a cybercriminal needs to gain access to your account. The following articles not only teach you about HOW to make secure passwords and protect them, but WHY as well.
-
How To Choose a Secure Password
-
Password Managers Are The Key To Secure Passwords
-
The Importance of Two-Factor Authentication
TRACK 2: Malware:
Malware, malware, malware! You hear that term everywhere, however, it can mean so many different things. Malware is more of an umbrella term used for any kind of malicious software on the Internet landscape- from annoying adware to devastating ransomware, these articles will help explain to you the types of common malware, what it does, and how you can get it.
-
Malware 101: What Is Malware?
-
Malware 101: How Do I Get Malware on My Computer? Part One
-
Malware 101: How Do I Get Malware on My Computer? Part Two
-
Ransomware- When Cybercriminals Hold Your Computer Hostage
TRACK 3: Privacy:
If this isn’t an issue for you, it should be. A lot of people take the stance of “I don’t do anything wrong, therefore I have nothing to hide.” however that is largely misinterpreted. You have everything to hide. So many apps, websites and services we use online today host a trove of data about their users, they’re a goldmine for a cybercriminal. These articles will teach you about the importance of data privacy and how to make your digital footprint more secure online.
-
How To Avoid Identity Theft Online
-
What Happens When Your Identity Is Stolen?
-
Data Privacy and Ridesharing Apps
-
Online Dating and Protecting Your Privacy
-
How To Protect Yourself From Cyberstalkers
TRACK 4:Data Breaches:
Data breaches are why we should care about our privacy. Scammers and criminals target companies in order to obtain as much data as possible about an individual, which in turn helps them commit identity theft or collect a hefty sum on the black market for the data. Learn about how data breaches happen and what to do if you happen to get involved in a data breach.
-
Data Breaches Aren't Going Away- What You Need To Know
-
Data Breach- The Best Defense is Vigilance
-
POS Malware Data Breaches and Why They Keep Happening
-
What To Do In The Event Of A Bank Breach
-
What to Do in the Event of a Major Data Breach
-
My Account May Have Been Hacked—What To Do Now?
-
What is Cyber Espionage?
TRACK 5:Safe Computing:
A lot of the threats today you can combat yourself, just armed with a little bit of knowledge. Internet security software is an essential piece of the cyber security pie, however, it can’t protect you form every single threat out there. Comprehensive Internet security software, coupled with a well educated user will go a long way on the threat landscape, so get your learn on, and empower yourself to navigate the web safely.
-
The Importance of General Software Updates and Patches
-
How To Protect Yourself From Phishing Scams
-
How To Safely and Securely Use USB Memory Sticks
-
SSL Certificates: What Consumers Need to Know
-
5 Ways You Didn't Know You Could Get a Virus, Malware, or Your Social Account Hacked
-
What is Social Engineering?
-
What Is A Man In The Middle Attack?
-
Public Wi-Fi Security 101: What Makes Public Wi-Fi Vulnerable To Attack And How To Stay Safe
TRACK 6: Online Scams:
Scammers are the bottom of the barrel of Internet criminals. Online scams take hardly any technical skills to execute, yet so many people fall for them. You can find online scams everywhere today, from social media platforms to our private email accounts. These articles can teach you how to identify the common red flags found in most scams, and how to keep protected against them.
-
Social Media Scams Based on Current Events
-
Free Movie And Television Scams On Facebook Comments Embedded In Popular Website Articles
-
How To Protect Yourself From Phishing Scams
TRACK 7: Mobile Protection:
There are just as many threats on the mobile landscape as there are with computers. With the popularity of smartphones and tablets on the rise, they are becoming more of a target to cybercriminals. Since we’re starting to use our smaller devices as we would a desktop or laptop computer, more of our personal data is stored on these devices and thieves are taking notice. Learn about the varied types of threats on the mobile landscape and how to stay safe.
-
Theft-Proof Your Mobile Data
-
Four Mobile Threats that May Surprise You
-
Mobile Scams: How-to Identify Them and Protect Yourself
-
How to Spot a Fake Android App
-
Cyber Security Concerns and Smartphones 

-
Exactly How Free Is That Free App?
Why to attend?
With members from around the world focused on learning about CYBER SECURITY AND ETHICAL HACKING this is your single best opportunity to reach the largest assemblage of participants from the Global Information Technology Community. Conduct demonstrations, distribute information, acquire knowledge about current and trending global technologies, make a splash with a new research, and receive name recognition at this 2-days event. World-renowned speakers, the most recent techniques, tactics, and the newest updates in the CYBER SECURITY are the hallmarks of this conference.
Issue with VISA!!
Are you planning to have a professional and delightful trip to London, UK???
We believe you must be having a query regarding your VISA to Visit as a Speaker/Delegate, Tourist or Business Person to London, UK. Cyber security 2020 Committee will be happy to help you in all regards to plan your trip to the most historic place London. Here is the simplest way to know the process for your Visa Approval. Kindly register for the conference at the earliest and drops us an email at secyber49@gmail.com and avail the official invitation letter from us and attend this event ahead with a closer step for approval of your VISA.Register/enrolhere to get an official invitation letter: https://cybersecurity.annualcongress.com/registration.php
Processing time for VISA applications may vary depending on the office and the time of the year. Delegates/Attendees are encouraged to submit their visa applications well in advance of the date of the event at a VISA Application Centre or online E-applications, including all supporting documents.
We’re here. Where are you?
Our conferences draw over 150 attendees per year, more than any other conference out there. Why? Because we’re the only event that offers such a broad range of reasons. Valuable content presented by some of the industry’s most forward-thinking leaders. The chance to network with thousands of peers. And the inspiration you need to protect your organization now and in the future. Once you attend, it’s hard not to get swept up in the opportunities to find new industry voices and new ways of approaching security.
So, want to be better prepared for tomorrow’s challenges? Connect with CYBER SECURITY Conference today. You’ll feel smarter for doing it.
Nowadays, companies are focusing not only on security solutions but also on security services. Among the services, managed security service is rapidly gaining traction by covering 40% of the security market in 2015. Managed security services help clients to prepare for cyber-attacks by understanding and managing cyber exposure, enabling them to make informed investment decisions and to put necessary, cost-effective protection in place.
Explosive increase in cyber threats is backed by factors such as increasing mobile and web usage and social media, among others. Also, Internet of Things (IoT) is another major factor that has invited various cyber threats at various sensors, terminals, and end devices. Considering this, every sector has a wide scope for cyber security requirement. Organizations are looking for integrated security solutions these days to cater their various security needs through one platform for cost benefits and to reduce complications. The aerospace, defense, and intelligence vertical needs the most advanced cyber security solutions due to increasing security need of the nations. E-governance, increasing concerns regarding territorial security like military, navy, and economic has led the government to think more seriously about cyber threats. Also, increasing demand for cyber security has led the government to make about stringent cyber and IT laws, legal and regulatory compliances, and data security.The major vendors in the cyber security market are IBM corporations, Intel Corporation, Booz Allen Hamilton, CSC, Lockheed Martin, Northr Grumman, Sophos, Symantec, and Trend Micro.
Grumman, Sophos, Symantec, and Trend Micro.
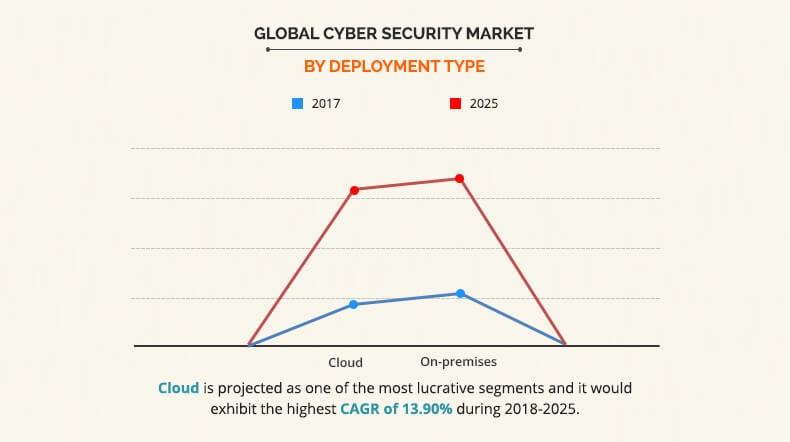
The global cyber security market is segmented based on component, solution/offerings, deployment type, user type, industry vertical, and region. In terms of component, the market is segmented into solution and services. The solution segment is again bifurcated into hardware and software. Based on solution/offerings, the market is segmented into identity and access management, infrastructure security, governance, risk, & compliance, unified vulnerability management service offering, and data security and privacy service offering. Based on deployment type, the market is divided into cloud and on-premises. By user type, the market is classified into large enterprises and small & medium enterprises. In terms of industry vertical, the market is segmented into aerospace and defense, BFSI, public sector, retail, healthcare, IT and telecom, energy and utilities, manufacturing, and others. As per region, the cyber security market size is analyzed across North America, Europe, Asia-Pacific, and LAMEA.
The global cyber security market is dominated by key players such as Accenture, Capgemini, Cognizant, HCL Technologies Limited, IBM Corporation, Symantec Corporation, Tata Consultancy Services, Wipro Limited, and others.
Cyber Security Market Outlook - 2025
The cyber security market size was valued at $104.60 billion in 2017 and is projected to reach $258.99 billion by 2025, growing at a CAGR of 11.9% from 2018 to 2025. Cyber security also referred to as Information Technology (IT) security, emphasize on safeguarding computers, programs, networks, and data from unlicensed or spontaneous access. As cyber threats have gained importance, security solutions have progressed as well. Factors such as rise in malware and phishing threats, and growth in adoption of IoT and BYOD trend among organizations, are driving the cyber security industry growth.









 Grumman, Sophos, Symantec, and Trend Micro.
Grumman, Sophos, Symantec, and Trend Micro.